How the protocol stack executes solicitations
Create a socket
Internal structure of protocol stack
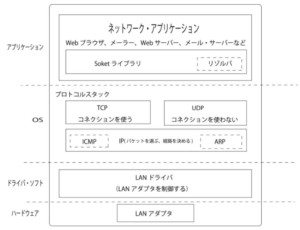
The internal structure of the protocol stack is divided into several parts with different roles. The configuration in the above figure is that the side requesting a work is on the upper side and the worker who receives the request is on the lower side. The highest one is “network application”, which is equivalent to programs such as browser, mailer, web server, and mail server. From here we request work such as data transmission and so on toward the category below the figure. The operation of sending and receiving data on the network by any application, not only the browser, is similar. Although the content of the data transmitted and received by the application is different, since the operation when sending and receiving data is common, the difference depending on the application disappears. In the lower part of the application there is a “Soket library”, below it “Resolver” is embedded. These perform the operation of querying the DNS server for the IP address. Below that represents the inside of the OS, there is a protocol stack here. At the top of the protocol stack is a part that transmits and receives data using the protocol “TCP”. There is a part that performs data transmission / reception using the protocol “UDP”, and these two perform the transmission / reception operation upon receiving a request from the application. Usual applications such as browsers and mails send and receive data using TCP, and use UDP when sending and receiving short control data by inquiries to the DNS server. Below that there is a part that controls transmission / reception operation using the IP protocol. When carrying data on the Internet, the data is divided into small pieces and carried in the form of “packet”, but the main role of IP is to carry the packet to the communication partner. The IP includes a part handling protocols called “ICMP” and “ARP”. ICMP is used to notify errors occurring when carrying packets and to notify messages for control. ARP is used to check the “MAC address” of the Ethernet corresponding to the IP address. “LAN driver” under IP controls the hardware of the LAN adapter, and the LAN adapter under the LAN adapter performs actual transmission / reception operation, that is, an operation of transmitting / receiving a signal to / from the cable. *: MAC address: The address used by the LAN type device standardized by IEEE is called the MAC address.
The entity of the socket is the control information for communication control
The protocol stack has a memory area for internally recording control information and records control information for controlling the communication operation therein. Information such as the number of IP addresses of communication parties, the port number, what kind of progress state the communication operation is, and the like are representative. There is no substance in the socket itself, but this control information can be said to be the substance of the socket. Alternatively, the memory area in which these control information is recorded may be called the entity of the socket.
The protocol stack operates with reference to this control information. Various control information for controlling the communication operation is recorded in the socket, and the protocol stack judges what to do next by referring to it.
Movement when calling socket
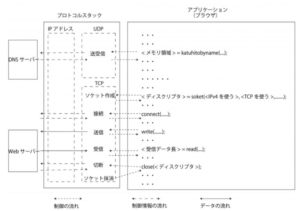
First, the browser asks the protocol stack to send and receive data using the TCP protocol via the Socket library. When the application asks the soket to create a socket as shown in the drawing phase, the protocol stack creates one socket according to the request. At that time, the protocol stack reserves a memory area for one socket. Since the memory area for recording the control information of the socket does not exist from the beginning, it is secured. Securing the memory area means to prepare a device to put the control information and record control information corresponding to the content therein. At this point, since the socket is just created, it is in the initial state in which transmission and reception has not yet begun, so control information indicating that it is in the initial state is recorded in the memory area of the socket. A socket is completed in this way. Next, the application is shown a “descriptor” to point to that socket. A descriptor is information that serves as a number tag to point to any one of a number of sockets inside the protocol stack. Upon receiving this descriptor, the application notifies the descriptor when requesting data transmission / reception to / from the protocol stack stack thereafter. Since records are recorded on the socket where and where it is communicating, what socket it is by the descriptor, all the necessary information is in the protocol stack Prove. This eliminates the need to have the application notify the communication partner information every time. *: The software module “memory management” manages the memory area.