Electronic signature and electronic authentication/electronic certificate
In modern times, when exchanging all kinds of information on the Internet, it is necessary to prove whether the other party of the exchange is the person who is not an impersonator, and whether or not the information can be trusted.
In the case of conventional paper documents such as contracts, credibility can be proved by affixing seals and signatures, but since information is exchanged on the Internet as “electronic documents”, signatures are electronically signed in the form of “electronic signatures” to verify identity, prevent spoofing, and prevent data falsification. Electronic authentication proves the credibility of electronic document exchanges.
Unlike the conventional paper document format, an electronic signature using an electronic certificate is applied to an electronic document, and electronic data can be exchanged safely on the Internet by being electronically authenticated.
Contents
- Electronic certificate
- Differences between digital signatures and digital certificates
- Mechanism of digital signature using digital certificate
- How certificate validation works
- Public key cryptography
Electronic certificate
An electronic certificate is for certifying the identity of an electronic signature (identity), and is a certificate issued by a third party called a certificate authority to certify the identity.
Since it is positioned as an alternative to the registered seal/seal certificate in paper document transactions, for example, when an agent makes an electronic application on behalf of the principal, the agent’s electronic certificate must be prepared at the same time as the principal’s electronic certificate.
There are two types of electronic certificates:
- Electronic certificate for signature
An electronic certificate for signature has a password consisting of 6 to 16 alphanumeric characters, and is used, for example, to create and send electronic documents in electronic applications with e-Tax.
- Electronic certificate for user certificate
The electronic certificate for user certificate consists of a four-digit PIN, and is mainly used when logging in to Internet sites. For example, when you apply online using your My Number Card. This makes it possible to prove that the login is by the person himself/herself.
Differences between digital signatures and digital certificates
The difference between an electronic signature and an electronic certificate is whether to prove the validity of the electronic contract itself or to prove the validity of the electronic signature.
Electronic signature
It corresponds to a seal or signature on paper media, and indicates only consent to the contents of an electronic document such as a contract by adding an electronic signature. (You cannot prove your identity.)
Digital certificate
An electronic certificate proves whether or not an electronic signature was made by the person himself/herself. Even if an electronic signature is given, the validity of the electronic document cannot be proved without the electronic certificate of the person himself/herself.
The credibility of electronic certificates is ensured by a certificate authority verifying the identity of the person.
When concluding an electronic contract, it is common to use an electronic signature and an electronic certificate as a set.
Digital Certificate Verifier
There is also a difference in the certifiers who certify the legitimacy between electronic signatures and electronic certificates.
In the case of an electronic signature, the person who made the electronic signature is the certifier, but in the case of an electronic certificate, the certificate authority, which is a third party organization, is the certifier.
There are two main types of certificate authorities: public certificate authorities and private certificate authorities.
- public certificate authority
Although the examination standards are strict, public certification authorities are generally used when concluding electronic contracts.
- Private Certificate Authority
It can be established by an individual or a legal entity. In some cases, private certificate authorities are used when internal documents and strict identity verification are not required.
Mechanism of digital signature using digital certificate
An electronic signature is an electronic signature applied to an electronic document, and solves the following two problems.
- Identity confirmation (that the document has not been tampered with)
- The intention of the signer himself/herself can be confirmed (confirming that the person signed the document)
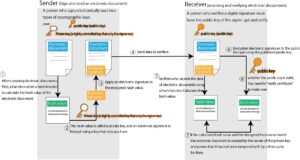
An electronic signature consists of two mechanisms called a public key cryptosystem and a hash value. The procedure is shown below.
-
When creating an electronic document, first calculate the hash value of the electronic document using a function called a hash function.
-
Encrypt this hash value using a private key, which is owned only by the person performing the electronic signature.
-
Digitally sign the encrypted hash value.
-
Send data to verifier.
-
After receiving the data, the verifier uses a hash function to calculate the hash value of the electronic document.
-
Decrypt the encrypted electronic signature using the publicly available public key.
-
If the calculated hash value and the decrypted hash value match, it proves that the electronic document was created by the owner of the private key and has not been tampered with by a third party.
-
Since the private key and public key are paired, the correct hash value cannot be calculated unless the keys match. Also, since the original data cannot be obtained from the hash value, an appropriate private key and public key are essential to confirm the hash value. To verify whether this private key and public key match, it is necessary to confirm by certificate verification.
hash value
A hash value is a value obtained from a given original text using a computational method that generates a random number of a fixed length (160 bits, 256 bits, etc.) with certain restrictions.
It is almost impossible to guess the original data from the hash value, and it is extremely difficult to create different data with the same hash value. This property is used to support communication encryption, user authentication, and electronic signatures.
How certificate validation works
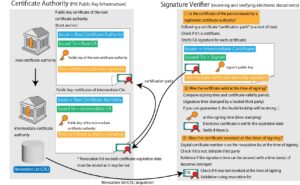
Certificate verification is verification of whether or not the public key corresponding to the private key used for signature is genuine, and confirms the following items.
-
Is the certificate issued to the signer by a legitimate certificate authority?
-
Was the certificate within its validity period at the time of signing?
-
Was the certificate revoked at the time of signing?
Role of PKI (Public Key Infrastructure) Certificate Authority
A certificate authority is an organization that issues digital certificates to guarantee the validity of a user’s public key in data communication using public key cryptography.
Certificate authorities play the following roles in the public key infrastructure.
-
issue a digital certificate that digitally signs the applicant’s public key;
-
Issue a CRL (Certificate Revocation List).
-
Publish the CPS (Certificate Authority Practice Statement).
-
Publish the public key of the certificate authority for validating digital certificates.
-
Strictly manage the private key of the CA.
A CRL is a list of revoked (distrusted) public key certificates that have expired but are no longer valid for authentication due to private key leaks, loss, certificate issuer rule violations, etc.
CRLs are updated from time to time by certificate authorities.
Public key cryptography
The encryption key is public (public key) so that anyone can use it, and the decryption key is strictly managed by the recipient.
Also, an encryption key and a decryption key are generated as a pair, and data encrypted with one encryption key can only be restored to the original data with the decryption key that is the pair of keys.
When performing encrypted communication with an unspecified number of parties, the sender encrypts with the receiver’s public key and the receiver decrypts with his own private key, but since there is a property that encryption and decryption can be performed with either key pair, the sender can encrypt with their own private key and the receiver can decrypt with the sender’s public key as in the digital signature procedure.
With digital signatures, this fact can be used to verify the data decrypted with the sender’s public key, making it possible to confirm the sender and whether or not the data has been tampered with.
Only one person has the private key corresponding to the public key, and the fact that the data can be decrypted correctly with the public key of the sender can be judged as proof that the data was sent from the sender who has the valid private key.
Therefore, the correct way for the sender to be verified is “the sender encrypts with his private key and the receiver decrypts with the sender’s public key”.