Public key, private key and common key
It is common knowledge that cryptography is used to exchange electronic data, but here we will explain the mechanism of cryptography using “keys” such as public keys, private keys, and common keys used for encryption and decryption. .
Strictly speaking, these keys refer to a mechanism for encrypting and decrypting data.
table of contents
- How public key cryptography works
- Advantages and disadvantages of public key cryptography
- Common key cryptography
- SSL connection method that combines public key cryptography and common key cryptography
- Effects of electronic data encryption
- Benefits of encryption
- Disadvantages of encryption
How public key cryptography works
Public key cryptography uses two keys to encrypt and exchange data.
These two keys are a “public key” and a “private key” created by the recipient.
Here, the public key can be obtained by anyone including the sender, but there is only one private key, and in this case only the receiver has it.
Therefore, the flow of public and private keys is as follows.
1. Recipient uses private key to create public key.
2. The sender receives the recipient’s public key.
3. The sender encrypts the plaintext using the public key and sends it to the receiver.
4. Recipient receives ciphertext
5. The recipient decrypts the ciphertext to plaintext with the private key.
Therefore, in public-key cryptography, only the recipient (the person who has the private key) can decrypt the encrypted plaintext.
The private key is kept only by the recipient, and the public key is published where anyone can obtain it.
Advantages and disadvantages of public key cryptography
The advantage of public key cryptography is high data security. It is a measure against threats such as “spoofing” and “eavesdropping”.
Since only one public key needs to be created and published, the public key can be easily managed.
The demerit is that the mechanism of encryption and decryption is complicated and the processing time is long. Compared to the common key cryptosystem, it is necessary to increase the data length of the key, and the processing takes time.
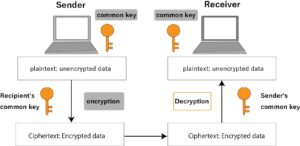
Common key cryptography
The public key cryptosystem uses two keys, a private key and a public key, but the common key cryptosystem uses only one key.
The data flow in this case is as follows.
1. The sender encrypts the plaintext using a common key.
2. The recipient uses the common key to decrypt the ciphertext into plaintext.
In this method, the same key (common key) is used for encryption and decryption.
Since the same key is used for encryption and decryption, strict management is required to prevent it from being stolen by a third party. In addition, as the number of parties to exchange data increases, the number of keys increases and the management method becomes complicated because the number of common keys increases accordingly.
For this reason, it can be said that the common key cryptosystem is suitable when there are few parties to exchange data.
SSL connection method that combines public key cryptography and common key cryptography
The SSL connection method is a combination of the public key cryptosystem and the common key cryptosystem.
In SSL connection, public key cryptography is used first, and a common key is used to encrypt the contents of communication, and the common key is shared between the sender and receiver. The private key is held only by the recipient.
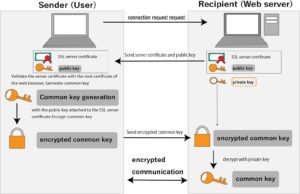
The data flow is as follows.
1. The sender requests permission to connect to send data to the receiver.
2. The recipient side that has accepted it sends the public key and SSL server certificate to the sender side.
3. The sender side checks the signature with the root certificate installed in the sender’s browser and verifies whether the SSL server certificate belongs to the receiver side.
4. Furthermore, the sender side generates a common key for encryption, encrypts the common key using the public key sent from the receiver side, and transmits it to the receiver side. (Encrypt common key and send)
5. Encrypt the electronic data with the sender’s common key and send it to the recipient.
6. The recipient side decrypts the encrypted and sent common key with the private key generated at the same time as the public key generated in 2.
7. The recipient side decrypts the received electronic data with the common key of 6 and obtains the data.
The sender generates a common key from the root certificate and server certificate. Based on the common key cryptosystem and the public key cryptosystem, after the plaintext is encrypted with the common key, the common key itself is also encrypted with the public key and sent to the receiver side.
The recipient decrypts the common key with the private key of the public key cryptosystem, and decrypts the plaintext encrypted by the common key cryptosystem.
As a concrete example,
Use this SSL connection method to register credit card numbers, etc. on EC sites, etc.
Since encrypted data is sent and received, the contents cannot be identified by a third party.
The SSL connection method is also applied to websites whose addresses begin with “https://~”.
Effects of electronic data encryption
Electronic data encryption refers to the process of transforming human recognizable information into an incomprehensible form. This process is usually done using a specific encryption key, which is also used to convert the data back into its original form (ie decrypt it). This makes it very difficult to understand the contents without the key, even if the data is stolen by a malicious party.
Benefits of encryption
Benefits of encryption include:
1. Data protection: An unauthorized access to encrypted information cannot be read without the proper key.
2. Protection of privacy: Personal data and confidential information are protected by proper encryption.
3. Legal compliance: Many industries, especially financial and healthcare industries, are required by law to encrypt customer information.
4. Ensuring credibility and trust: Customers and partners have a higher sense of trust when their data is properly protected.
Disadvantages of encryption
Disadvantages of encryption include:
1. Poor Performance: The encryption process can affect the performance of your computer system. Especially when large amounts of data need to be encrypted and decrypted, the process is time consuming and resource consuming.
2. Risk of lost keys: Loss of encryption keys can make it difficult or impossible to access encrypted data.
3. Software Compatibility: Not all software or systems support all encryption standards, so compatibility issues can arise.
The above is the effect of encryption and the advantages and disadvantages of each. To properly protect electronic data, it is important to consider all of these factors and plan and implement appropriate encryption methods. The right combination of encryption protocols and key management can strike the right balance between security and performance.
You also need a good key management policy to prevent key loss. This should include key creation, storage, distribution, renewal, and destruction. Additionally, if encryption of data is required, it is necessary to ensure that the software and hardware required to access the data support encryption.
Finally, it is important to understand that encryption alone does not solve all security problems. Encryption is part of security measures and should be used in combination with other measures (e.g., secure password policies, two-factor authentication, use of software that adheres to security best practices, etc.).